Understanding Remote Code Execution Vulnerabilities and Protection Measures
Remote Code Execution (RCE) vulnerabilities are a critical type of cyber threat where attackers execute arbitrary or malicious code on a target machine. This usually occurs through vulnerable software applications or services, allowing attackers to conduct various malicious activities, including data theft, system compromise, and the installation of malware or ransomware. In some cases, the compromised system may be used to launch further attacks.
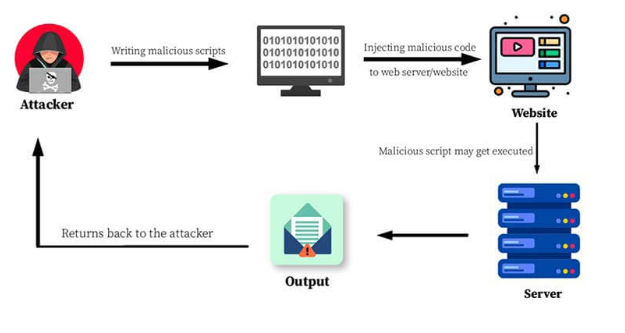
To protect against RCE attacks, it’s essential to adopt secure computing practices. These include keeping software up-to-date, using strong passwords, and being cautious about suspicious emails and links.
Arbitrary Code Execution Defined
Arbitrary code execution involves running code or commands on a system without restrictions or protections, which can lead to unauthorized or harmful actions such as data theft, file destruction, and system control.
Example:
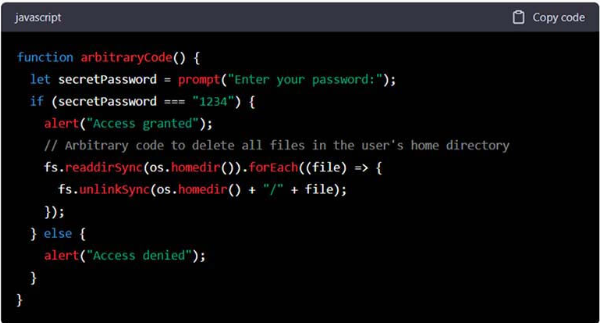
Important: Do not execute this code. This example demonstrates a code that prompts the user for a password and, if correct, deletes all files in the user’s home directory, potentially causing irreversible damage. This highlights the severe threat posed by arbitrary code execution.
Origins and Reasons for RCE Attacks
RCE attacks have roots tracing back to the early computer and network systems era. As these systems became more interconnected, the potential for exploitation increased, necessitating security measures like firewalls and data encryption. Despite advancements in security, attack methods have also evolved, becoming more sophisticated.
The proliferation of software vulnerabilities is a significant factor behind the rise in RCE attacks. As software complexity and usage have grown, so has the number of exploitable vulnerabilities, providing attackers with a broad range of targets. Additionally, in today’s digital landscape, data has become incredibly valuable, making RCE attacks a lucrative method for accessing sensitive information.
RCE attacks are facilitated by several factors:
- Software Vulnerabilities: Exploiting flaws in software systems.
- Inadequate Validation: Insufficient validation of remote machine and user inputs can allow attackers to execute code remotely.
- Outdated Software: Older software versions are often more vulnerable.
- Weak or Default Passwords: Easy-to-guess credentials can provide attackers with access.
- Social Engineering: Deceiving individuals into running malicious code.
- Third-Party Integrations: Introducing vulnerabilities through external software or code.
- Malicious File Downloads: Using harmful files to execute code on a system.
Types of RCE Attacks and Examples of Known Vulnerabilities
RCE attacks manifest in various forms, including:
- Command Injection: An attacker exploits an application vulnerability by injecting arbitrary commands. This involves sending a malicious payload to the application, which then executes the injected command.
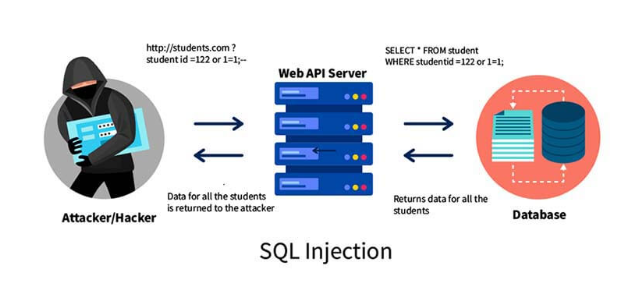
- SQL Injection: This attack involves exploiting a database vulnerability by injecting malicious SQL code. Attackers can alter database data or gain system access through this method.
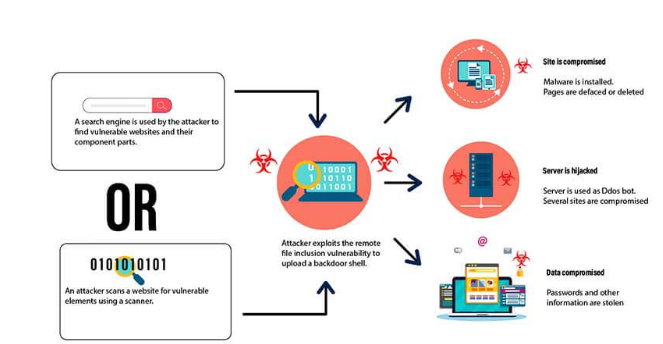
- Remote File Inclusion: This attack occurs when a file from a remote server is included in a web application, allowing the attacker to execute arbitrary code.
- Cross-Site Scripting (XSS): In XSS attacks, attackers inject malicious scripts into web applications to steal data, redirect users, or execute code.
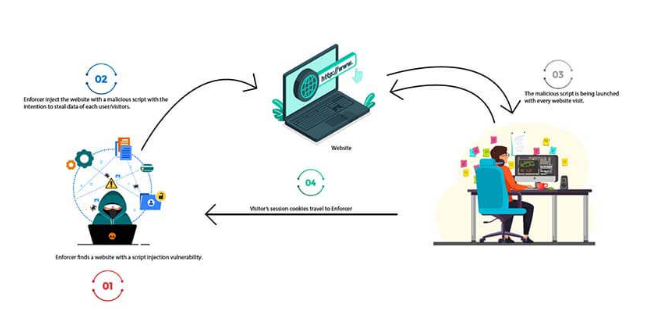
Illustration of SQL Injection and Remote File Inclusion
Notable RCE Vulnerabilities:
- Windows SMB RCE (WannaCry) – CVE-2017-0143
- Microsoft Windows RCE – CVE-2019-0708
- Adobe Flash Player RCE – CVE-2018-4878
- Google Chrome RCE – CVE-2023-0928
- Oracle WebLogic Server RCE – CVE-2019-2725
- VMware vCenter Server RCE – CVE-2021-21972
- Microsoft Exchange Server RCE – CVE-2021-26855
Impact of RCE Attacks
RCE attacks can have severe consequences, including:
- Data Theft: Stealing sensitive information such as financial records, personal details, intellectual property, and trade secrets.
- Malware Propagation: Spreading malware or viruses, potentially causing widespread harm and disruption.
- System Compromise: Gaining full control of a system, enabling actions like data theft, system memory manipulation, backdoor installation, command execution, and system setting modifications.
- Service Disruption: RCE attacks can be used to launch denial of service (DoS) or distributed denial of service (DDoS) attacks, making systems or web applications inaccessible.
- Reputation Damage: A successful RCE attack can tarnish a company’s or individual’s reputation, leading to legal liabilities, loss of revenue, and regulatory fines.
- Financial Loss: Costs associated with asset theft, revenue loss, and recovery efforts can be significant.
Detecting RCE Vulnerabilities
Finding RCE vulnerabilities requires a combination of approaches:
- Manual Testing: This is crucial for detecting vulnerabilities that automated scanners might miss. It involves testing for code injection and execution in web user input fields, manipulating traffic, and exploiting known software flaws. Tools like Metasploit, Nmap, and Burp Suite can be used for these purposes.
- Code Review: Inspecting code for vulnerabilities such as buffer overflows, SQL injections, and cross-site scripting (XSS) attacks is essential.
- Monitoring for Suspicious Activity: Use network and system monitoring tools to detect unusual behavior indicative of RCE attacks.
- Understanding the Technology: Familiarity with the programming languages, web frameworks, and third-party libraries used in the system can help identify potential issues.
- Vulnerability Scanning: Regular scans with automated tools can quickly identify common RCE attack vectors and vulnerabilities.
Addressing RCE Vulnerabilities
Key steps to fix RCE vulnerabilities include:
- Patching: Regularly updating software and systems to the latest versions with security patches is crucial. This applies to operating systems, applications, and libraries, helping to prevent the exploitation of known vulnerabilities.
- Secure Coding Practices: Adopting secure coding standards and conducting regular code reviews can help identify and mitigate vulnerabilities.
- Code Signing: This ensures that the software has not been tampered with and is from a trusted source.
- Network Segmentation: Segregating critical assets can limit the spread of malware and reduce the impact of a breach.
- Principle of Least Privilege: Granting users and systems only the permissions necessary for their roles helps minimize potential damage.
- Secure Configurations: Ensuring that systems, devices, and applications are configured securely reduces the risk of exploitation.
Long-Term Prevention Strategies
To maintain long-term security against RCE attacks, consider the following strategies:
- Software Updates: Keep all software, including operating systems and applications, up-to-date with the latest versions and patches, as they often include fixes for security vulnerabilities.
- Disable Unnecessary Services: Reducing the number of active services minimizes the system’s attack surface.
- Cautious Email Handling: Be wary of opening email attachments, especially from unknown sources, as they can be vectors for malware.
- Two-Factor Authentication: Adding an extra layer of security helps protect accounts even if passwords are compromised.
- Incident Response: Quickly disconnecting an infected system from the network can prevent the spread of an attack.
- Security Team Notification: Promptly informing the security team or IT department can help contain and address the attack.
- System Isolation: Isolating affected systems can prevent the attack from spreading further.
- Disable Remote Access: If an attack involves remote access tools, disabling such access can thwart ongoing attempts.
Detection Strategies
To detect RCE attacks effectively, use:
- Intrusion Detection Systems (IDS): These systems monitor network traffic and alert administrators to unusual activities, helping to identify and mitigate attacks.
- Log Monitoring: Analyzing system logs can reveal suspicious patterns or actions that may indicate an RCE attack.
- Endpoint Security: Software designed to monitor and protect endpoints can detect suspicious activity and alert administrators.
- Behavioral Analysis: Tools that analyze behavior can identify anomalies that might indicate an RCE attack.
- Vulnerability Scanning: Regular scans help identify potential vulnerabilities that could be exploited in RCE attacks.
Patch management tools like Patch My PC automate the process of keeping systems updated, reducing the risk of RCE and other vulnerabilities. This service helps ensure that systems are protected from known vulnerabilities and reduces the effort required to maintain a secure IT environment.
Summary
This overview covered what RCE vulnerabilities are and how to prevent and address them. Patch management is a crucial aspect of effective vulnerability control, and integrating third-party patch management for platforms like Microsoft and Intune can enhance IT security. By automating the packaging of third-party applications and updates, Patch My PC helps organizations stay secure, save time, and reduce costs associated with managing vulnerabilities.












