What Is Penetration Testing?
Penetration testing is an organized security testing that is conducted by an outsourced security team or company. The testers make simulation attacks in the real world in limited time span which is typically few days to few weeks. The company is presented with a report at the end of the assessment with vulnerabilities found and remediation advice. Penetration tests can be applied to achieve the security baseline and compliance, as well as determine the easily noticeable flaws. After the test is however completed no further testing is done except in case another test is scheduled. This will produce long lapses whereby fresh vulnerabilities can go unnoticed.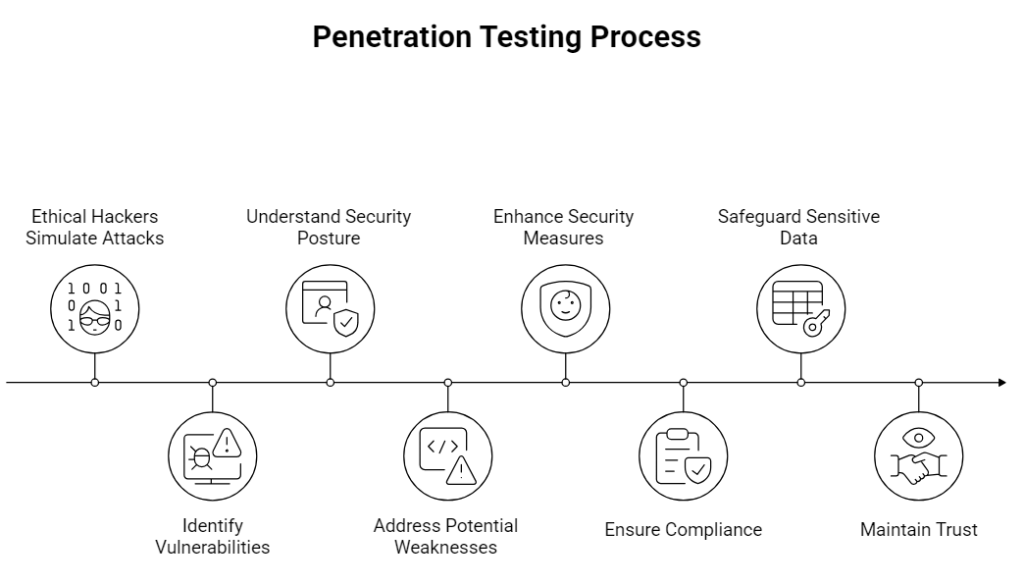
What Is Bug Bounty Testing?
The Bug bounty programs do otherwise. Rather than engaging one set of testing team on a temporary basis, the companies have embraced the services of a community of ethical hackers who constantly test systems within specified rules. Security model is provided only when security researchers discover valid vulnerabilities of the product, which results in performance-based security model that is developed as the product advances. Bug bounty programs offer sustained testing, attacker insights into the system, and more rapid exposure to new vulnerabilities as the systems evolve. This particularly suits them with contemporary digital products that are frequently updated.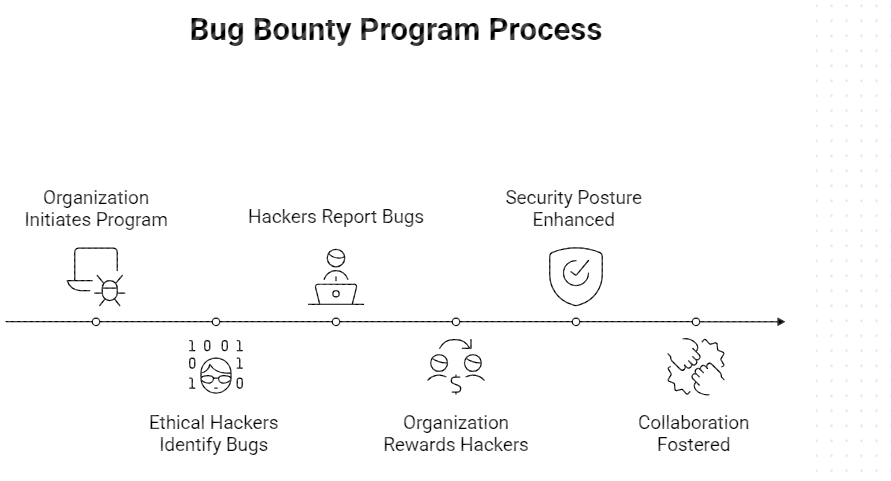
Key Differences That Matter
Continuity and scale forms the most significant point of departure between penetration testing and bug bounty. Penetration testing is an intermittent and time and budget-constrained activity. Bug bounty programs are open and reusable and can be operated by different researchers working on the same systems at the same time. It results in more extensive coverage and quicker vulnerability discovery. Another significant difference is cost structure. Penetration tests have initial payments whether successful or not. Bug bounty programs enable the companies to only pay per confirmed vulnerability, which is more efficient and result-oriented in security spending.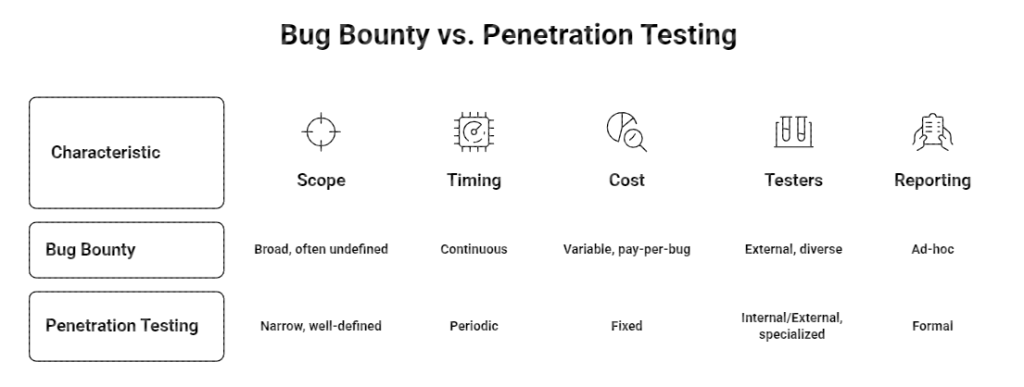
Which Model Fits Modern Businesses Better?
Continuous security testing is necessary in companies where the new features are issued frequently, the company applies APIs and deals with user sensitive data. They cannot offer a prolonged protection in such environments using a one-time penetration test. The nature of bug bounty programs is flexible to an on-going development process and offers sustained transparency on the emerging risks. This does not imply that penetration testing is not valuable. It is also still used in compliance mandates and setting up baseline security. Nevertheless, its use and dependence alone exposes companies to intervals between tests.Why Bugv Is the Practical Choice in Nepal
Bugv is a localized bug bounty project that targets the Nepal digital infrastructure and startup ecosystem. It matches companies with white hat hackers, administers responsible disclosure, certifies vulnerability reports, and hosts live testing sessions. This enables business organisations to use bug bounties without creating elaborate in-house security activities. With Bugv, companies receive to the ongoing testing, economically efficient security enhancements, and quicker vulnerability detection, all within a systematized and responsible system.Final Thoughts
Penetration testing or bug bounty is not an issue of which one is superior in theory, but which one is superior in the present-day digital business. Continuous testing is always better than periodic testing, especially in fast changing environments. Bug bounty programs offer that continuity at the cost of maintaining cost-directed results. When you are just conducting periodic penetration tests on your company, you are exposing the company to serious security lapses between tests. Bugv assists companies in Nepal to embrace structured bug bounty programs which offer round-the-clock security testing. Get your platform hacked smarter at Bugv.
Comments from Facebook