Authentication mechanisms are the backbone of web security, ensuring that only authorized users gain access to sensitive areas of an application. However, security researchers and bug bounty hunters often discover ways to bypass these mechanisms, exposing vulnerabilities that attackers could exploit. In this blog, we will explore the most common authentication bypass techniques used in bug bounty programs and how you can protect your applications from them.
Why Authentication Bypass Matters
Authentication bypass vulnerabilities allow unauthorized users to gain access to restricted areas, potentially exposing sensitive information, modifying data, or even taking over user accounts. Such flaws can lead to serious security breaches and data leaks, making them a critical issue for developers and security professionals.
Common Authentication Bypass Techniques
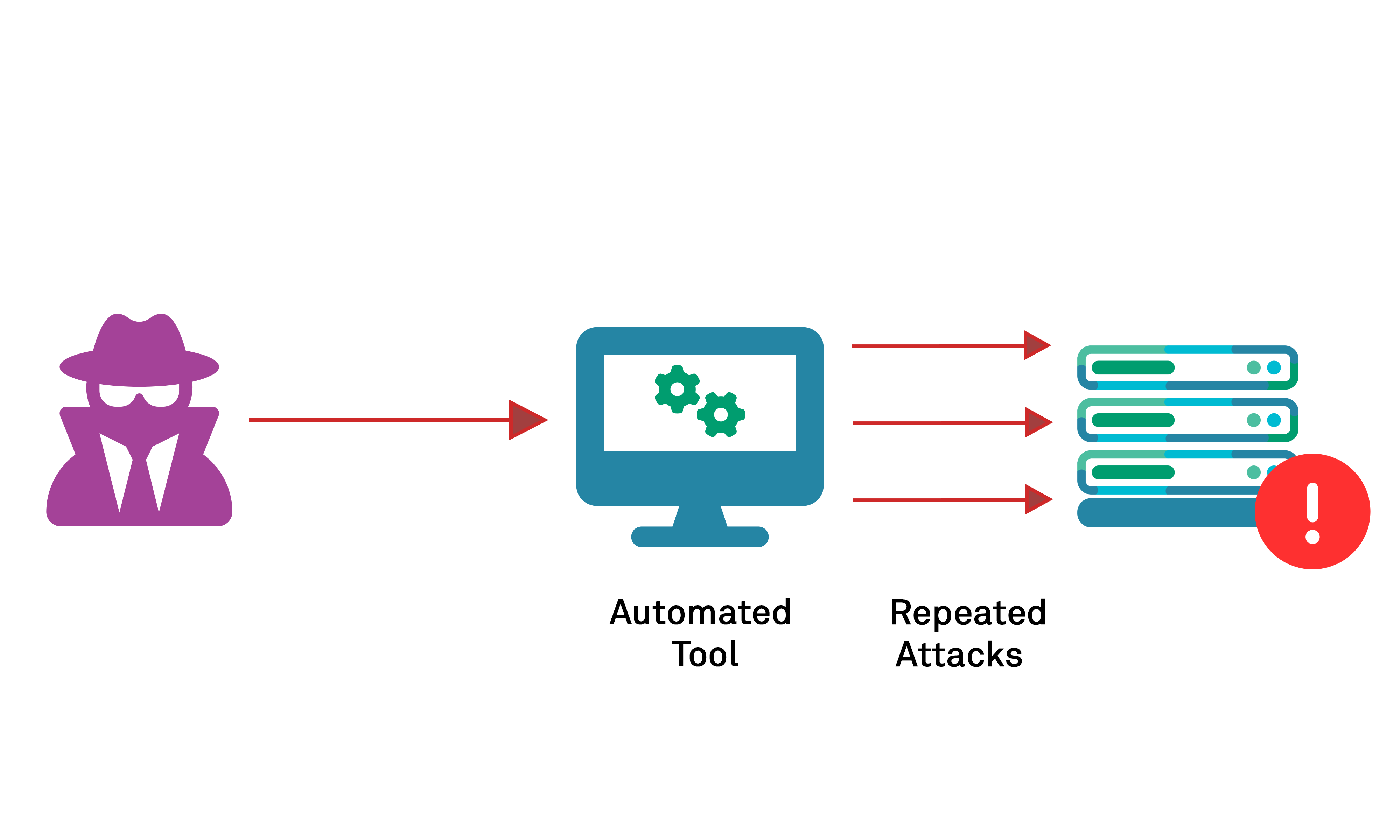
1. Brute Force Attacks
Brute force attacks involve guessing login credentials by systematically trying different username-password combinations. Attackers often use automated tools to speed up the process. Weak passwords and lack of rate limiting make this attack feasible.
How to Prevent:
- Implement rate limiting and account lockout policies.
- Use CAPTCHA to deter bots.
- Encourage strong password practices.
- Implement passwordless authentication where feasible.
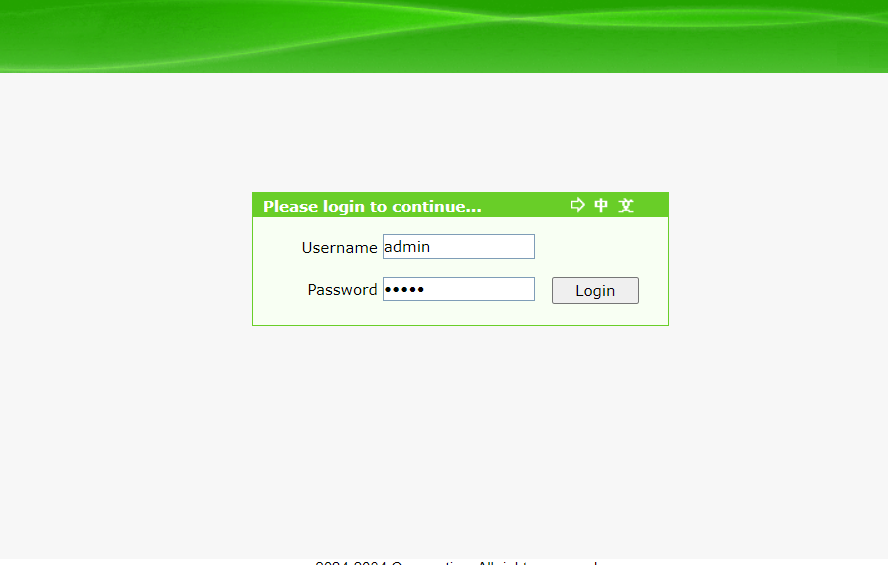
2. Default Credentials
Many applications ship with default usernames and passwords that are easily guessable (e.g., admin/admin, root/root). Attackers exploit this by trying known default credentials.
How to Prevent:
- Enforce password changes on first login.
- Disable or remove default accounts.
- Regularly audit user accounts for weak or unchanged credentials.
3. Weak Session Management
Poor session handling can allow attackers to hijack authenticated sessions, granting unauthorized access. Issues like predictable session IDs, lack of expiration, and weak cookie security contribute to this vulnerability.
How to Prevent:
- Use secure, unique session tokens.
- Implement session expiration and logout mechanisms.
- Use HTTPOnly, Secure, and SameSite flags for cookies.
- Revoke sessions on password changes or logout.
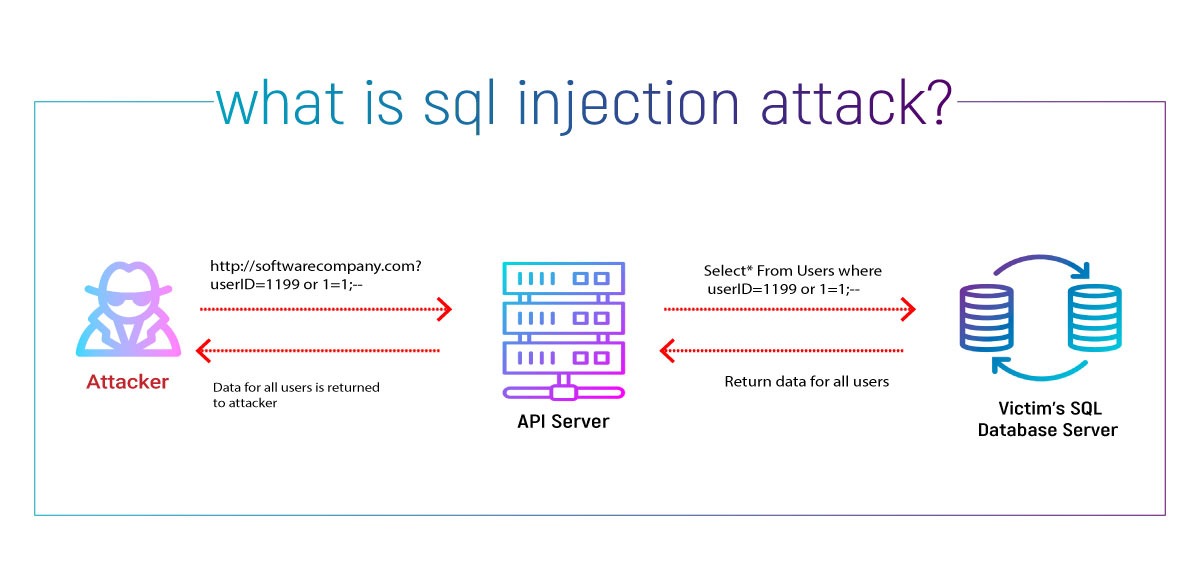
4. SQL Injection in Login Forms
SQL injection attacks allow attackers to manipulate login queries to bypass authentication. A common trick is injecting ' OR '1'='1 into input fields, which always evaluates as true.
How to Prevent:
- Use prepared statements and parameterized queries.
- Sanitize and validate all user inputs.
- Implement Web Application Firewalls (WAFs) to block malicious requests.
5. Bypassing 2FA (Two-Factor Authentication)
Attackers attempt to bypass 2FA using various techniques such as brute-forcing one-time passwords (OTPs), intercepting SMS-based codes, or abusing fallback mechanisms like email recovery.
How to Prevent:
- Use phishing-resistant authentication methods like FIDO2.
- Implement rate limiting on OTP attempts.
- Disable fallback mechanisms if not necessary.
- Use app-based or hardware token authentication instead of SMS-based 2FA.
6. Password Reset Exploits
Poorly implemented password reset mechanisms can allow attackers to reset passwords without proper verification, leading to account takeovers.
How to Prevent:
- Use secure token-based password resets with unique, time-limited tokens.
- Require verification via email or phone.
- Implement expiration times for reset links and invalidate them after use.
7. IDOR (Insecure Direct Object References)
IDOR vulnerabilities occur when an application improperly validates user access to resources, allowing attackers to modify parameters to access unauthorized accounts.
How to Prevent:
- Enforce strict access control checks.
- Use UUIDs instead of sequential user IDs.
- Implement proper authentication checks on API endpoints.
8. OAuth and SSO Misconfigurations
Improperly configured OAuth and Single Sign-On (SSO) implementations can allow attackers to authenticate as other users or gain access without credentials.
How to Prevent:
- Validate OAuth tokens properly.
- Implement strict redirect URI validation.
- Use PKCE (Proof Key for Code Exchange) for OAuth flows.
9. Logic Flaws in Authentication
Sometimes, developers introduce logical errors that let attackers bypass authentication without needing credentials. These flaws often arise from incorrect state management, insecure workflows, or inconsistent validation.
How to Prevent:
- Conduct thorough security testing and code reviews.
- Implement proper validation and error handling.
- Regularly review authentication logic for anomalies.
10. Exploiting JWT (JSON Web Token) Weaknesses
JWT tokens are used for authentication, but misconfigurations can allow attackers to forge tokens or exploit weak signing algorithms, leading to unauthorized access.
How to Prevent:
- Use strong algorithms like RS256 instead of HS256.
- Never expose private keys.
- Implement proper token validation.
- Set token expiration times and avoid long-lived tokens.
How to Protect Your Application from Authentication Bypasses
Authentication bypass vulnerabilities can be mitigated by following robust security practices. Here are some key preventive measures:
- Implement Multi-Factor Authentication (MFA): Adding an extra verification step significantly reduces the risk of unauthorized access, even if login credentials are compromised.
- Enforce Strong Password Policies: Require users to create complex passwords and avoid using common or default passwords. Implement mechanisms like password hashing (bcrypt, Argon2) to securely store credentials.
- Use Secure Session Management: Ensure session tokens are unique, securely stored, and automatically expire after a period of inactivity. Implement proper logout mechanisms and prevent session fixation attacks.
- Validate and Sanitize User Inputs: All inputs, especially those affecting authentication mechanisms, should be properly sanitized and validated to prevent injection attacks.
- Implement Rate Limiting and Account Lockout: Restrict the number of failed login attempts to prevent brute-force attacks. Implement CAPTCHA challenges for suspicious activity.
- Regular Security Audits and Penetration Testing: Conduct regular vulnerability assessments to identify and patch security loopholes. Ethical hackers and security researchers can help uncover flaws before malicious actors exploit them.
- Monitor and Log Authentication Events: Maintain logs of authentication attempts and unusual login activities. Enable real-time alerts for suspicious behavior, such as multiple failed logins or unauthorized access attempts.
- Ensure Secure Implementation of OAuth and SSO: Properly configure OAuth and SSO protocols to prevent authentication bypass via token forgery or misconfigurations. Use strong validation mechanisms for tokens and redirect URIs.
Conclusion
Authentication bypass vulnerabilities are a major concern in web security. By understanding the common techniques used by attackers and implementing strong security measures, organizations can better protect their applications from unauthorized access. Bug bounty hunters play a crucial role in discovering these flaws and helping companies secure their systems.
Stay secure, and keep hunting! 🚀
Need professional security testing? Bugv offers expert penetration testing services to identify and fix authentication flaws before attackers can exploit them. Contact us today!












