Understanding XML Injection: A Comprehensive Guide
Introduction
Data interchange between computers is essential in today’s digital environment, and XML (eXtensible Markup Language) is a key component of this process. Like any technology, XML is not impervious to security flaws, though. A vulnerability of this kind is XML Injection. This blog seeks to explain the nature of XML Injection, its mechanisms, possible consequences, and countermeasures.
What is XML Injection?
One kind of attack called XML Injection is when malicious XML content is manipulated or injected into an application that handles XML data. The intention is to take advantage of flaws in the XML parsing procedure, which may allow for data corruption, illegal access, or even total system compromise.
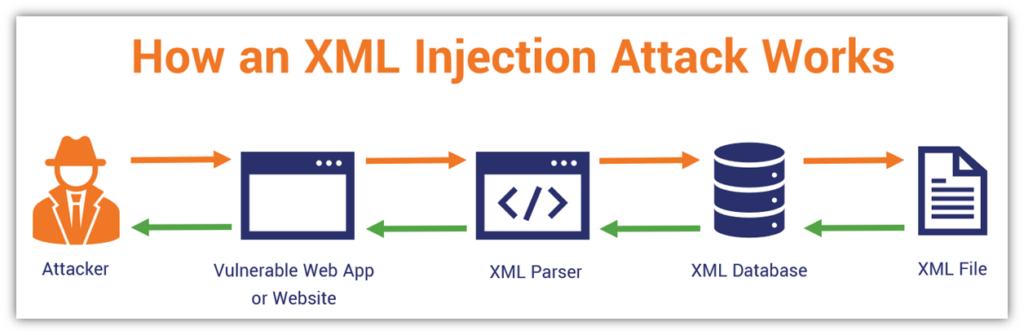
How Does XML Injection Work?
When user input is entered into XML documents without being properly validated or sanitized, applications are vulnerable to XML Injection. This is a simple example that shows how XML Injection functions:
- User Input Incorporation: An application takes user input and embeds it in an XML document.
- Malicious Input: An attacker provides specially crafted input containing malicious XML tags or entities.
- XML Parsing: The application processes the XML document without proper validation, allowing the malicious content to execute or alter the document structure.
Example Scenario
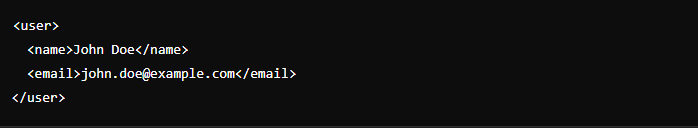
Consider a web application that uses XML to store user information. A typical XML structure might look like this:
An attacker could provide input like:
The resulting XML document might become:
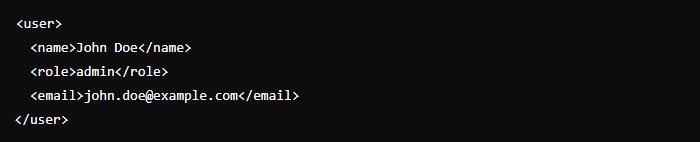
If the application does not properly validate this input, the attacker could escalate privileges or alter user roles.
Potential Impact of XML Injection
- Unauthorized Access: Attackers can gain access to sensitive data or functionality.
- Data Corruption: Malicious input can corrupt or delete data.
- Denial of Service (DoS): Large or complex XML payloads can overwhelm the XML parser, leading to service disruptions.
- Code Execution: In some cases, XML Injection can lead to arbitrary code execution, compromising the entire system.
Preventing XML Injection
Preventing XML Injection requires a combination of best practices in input validation, XML processing, and overall application security:
- Input Validation and Sanitization: Always validate and sanitize user input before incorporating it into XML documents. Use whitelisting approaches to allow only expected data formats.
- Parameterized Queries: When interacting with databases, use parameterized queries to prevent injection attacks.
- XML Parser Configuration: Configure XML parsers to disable external entity references (XXE) and other potentially dangerous features.
- Use Secure Libraries: Utilize secure libraries and frameworks that are designed to handle XML data safely.
- Regular Security Testing: Conduct regular security testing, including code reviews and penetration testing, to identify and address potential vulnerabilities.
Conclusion
If left unchecked, XML Injection is a powerful attack vector with potentially disastrous results. Developers and organizations can safeguard their applications from XML Injection by comprehending its mechanisms and putting strong security measures in place. At bugv, we value security above everything else in the development process and are dedicated to assisting you in protecting your apps from these kinds of risks.
Stay vigilant, stay secure!