Open-source tools have become an essential part of modern businesses, offering cost-effectiveness, flexibility, and a collaborative development model. From small startups to large enterprises, organizations rely on open-source software to streamline operations, reduce costs, and foster innovation. However, these benefits come with hidden risks that can have severe implications if overlooked.
In this blog, we will explore six critical risks of open-sourcing tools and how they can impact the security, compliance, and operational stability of an organization.
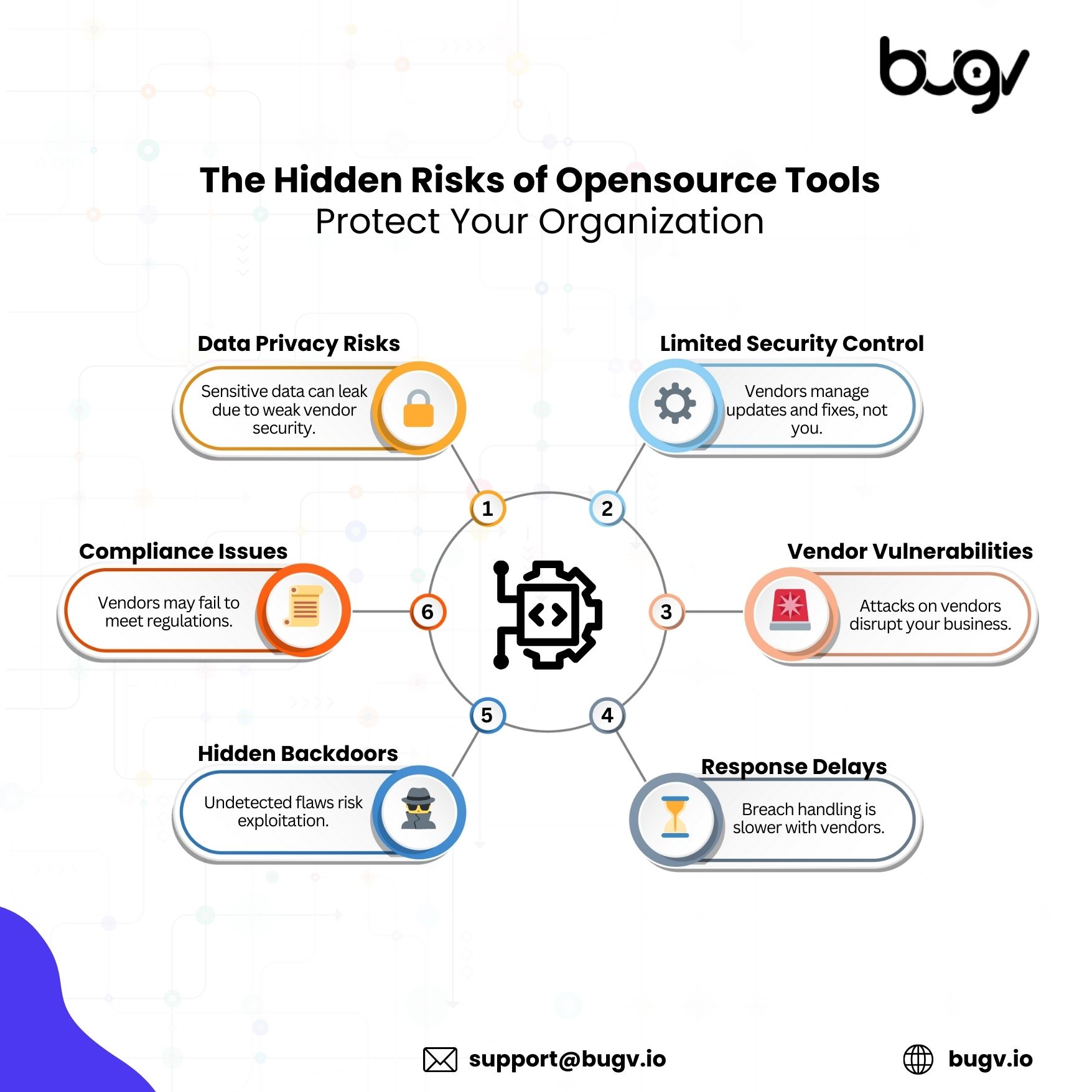
1. Security Flaws: Public Code, Public Risk
One of the most attractive aspects of open-source tools is their transparency—anyone can access, inspect, and modify the source code. While this fosters innovation and community-driven problem-solving, it also creates opportunities for malicious actors to exploit vulnerabilities.
For instance, attackers can analyze publicly available code to identify and exploit weaknesses before they are patched. High-profile vulnerabilities like the Log4Shell exploit in the widely-used Log4j library demonstrate how security flaws in open-source software can have global repercussions.
How to Mitigate This Risk:
- Regularly monitor for vulnerabilities in open-source tools used by your organization.
- Implement automated patch management to ensure timely updates.
- Use vulnerability scanners to identify and address weaknesses proactively.
2. No Accountability: The Decentralized Nature of Open Source
Unlike proprietary software backed by dedicated development teams, open-source projects rely on voluntary contributions. There’s no centralized authority responsible for maintaining, updating, or patching the software.
This lack of accountability can leave organizations exposed if the community supporting a tool loses interest or disbands. For example, if a project becomes outdated, organizations may face prolonged periods of vulnerability or compatibility issues with newer technologies.
How to Mitigate This Risk:
- Assess the health and activity of the community supporting the tool.
- Develop in-house expertise to maintain and update critical open-source tools.
- Establish contingency plans for replacing or maintaining abandoned projects.
3. Low Quality: Variability in Contributions
Open-source projects often welcome contributions from developers of all skill levels. While this inclusivity drives innovation, it also results in variability in code quality. Some contributions may lack rigorous testing or introduce unintended bugs.
Low-quality code can lead to operational inefficiencies, reduced performance, and security vulnerabilities. Organizations integrating open-source tools into critical systems must thoroughly vet their quality and reliability.
How to Mitigate This Risk:
- Perform thorough code reviews before implementing open-source tools.
- Use static and dynamic code analysis tools to evaluate quality and performance.
- Partner with third-party experts for audits of critical systems.
4. Dependency Issues: Over-Reliance on Community Support
Many open-source tools depend on a network of developers and contributors for ongoing maintenance and support. However, if the community loses interest or shifts focus, critical updates and bug fixes may be delayed or neglected altogether.
Dependency issues can leave organizations vulnerable to emerging threats or prevent them from adopting newer technologies that require compatibility updates.
How to Mitigate This Risk:
- Maintain an updated inventory of all open-source tools and their dependencies.
- Use dependency management tools to track and address outdated libraries.
- Allocate resources for in-house maintenance of essential tools.
5. Licensing Risks: Misuse Can Lead to Legal Trouble
Open-source software is distributed under specific licenses, such as the MIT License, GNU General Public License (GPL), or Apache License. These licenses dictate how the software can be used, modified, and distributed. Misinterpreting or violating these terms can result in legal disputes, financial penalties, or reputational damage.
For example, using software under a restrictive license without adhering to its terms, such as disclosing modifications or providing attribution, can lead to unintended consequences.
How to Mitigate This Risk:
- Conduct a thorough legal review of open-source licenses before adoption.
- Train your development team on the implications of various open-source licenses.
- Use license-compliance tools to ensure adherence to licensing terms.
6. Hidden Threats: Malicious Contributions and Backdoors
While open-source software relies on community contributions, not all contributors have good intentions. Malicious actors may introduce backdoors, malware, or other harmful code into a project, which can remain unnoticed without rigorous review processes.
Such hidden threats pose significant risks, especially for organizations integrating open-source tools into critical systems. If exploited, they can lead to data breaches, operational disruptions, or financial losses.
How to Mitigate This Risk:
- Implement strict code review processes to identify and prevent malicious contributions.
- Use automated tools to scan for suspicious or malicious code.
- Collaborate with trusted security experts for audits of open-source projects.
Balancing the Benefits and Risks of Open-Sourcing Tools
Open-source tools undoubtedly offer numerous advantages, from cost savings to increased innovation. However, their risks must not be overlooked. By adopting a proactive approach to security, quality assurance, and compliance, organizations can harness the power of open-source tools while mitigating potential downsides.
Key Recommendations:
- Regularly monitor open-source tools for updates and vulnerabilities.
- Invest in security solutions, such as penetration testing, to safeguard your systems.
- Build in-house capabilities to address risks and maintain critical tools.