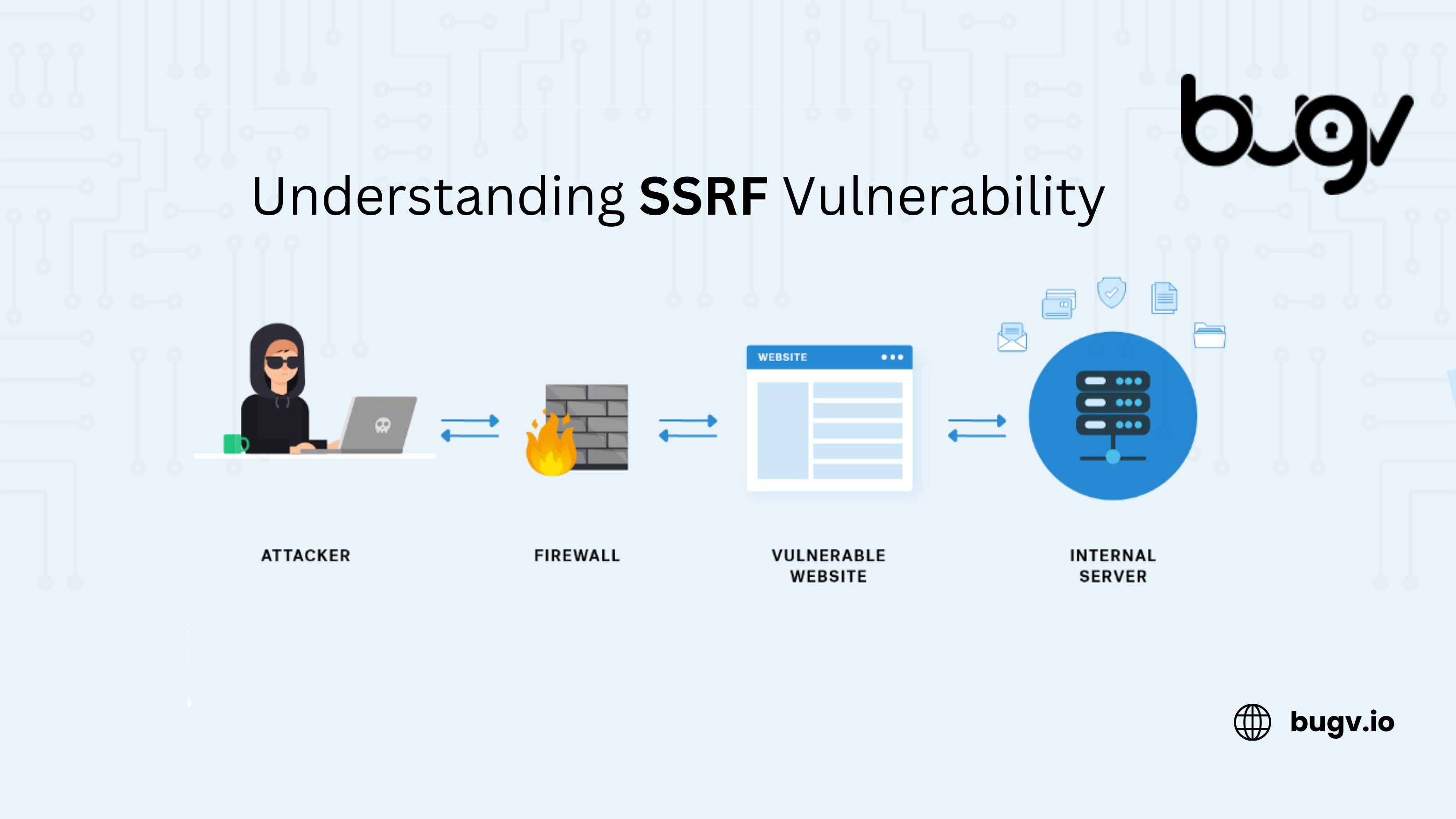
Server-Side Request Forgery (SSRF) is a highly impactful vulnerability that allows attackers to manipulate a server into making requests to unintended locations, often bypassing security restrictions. SSRF is especially critical in cloud environments and services that interact with internal networks or other resources.
In this blog, we will explore the SSRF vulnerability in detail, how it works, its potential consequences, and strategies for mitigation. By the end of this post, you’ll have a solid understanding of why SSRF is such a dangerous threat and how to protect your systems against it.
What is SSRF?
Server-Side Request Forgery (SSRF) occurs when an attacker is able to manipulate a vulnerable server into making requests to arbitrary resources, such as internal services or third-party servers, on behalf of the attacker. Essentially, the server acts as a proxy for the attacker’s request, making it harder for traditional security measures to detect or block the attack.
SSRF vulnerabilities typically arise when an application accepts URLs or IP addresses as user input, but fails to validate or sanitize this input adequately before making network requests. Attackers exploit this weakness to craft malicious requests that target internal servers, databases, cloud metadata, or other sensitive systems.
How Does SSRF Work?
To better understand SSRF, let’s break it down into a simple example:
- Vulnerable Application: A web application has a feature that allows users to enter a URL, which the server then fetches to display content from the external resource.
- User Input: The attacker enters a URL or IP address in a form, but the server does not properly validate the input.
- Server Request: Instead of requesting data from an external website (e.g.,
http://example.com), the attacker manipulates the URL to target an internal service. For instance, the attacker might change the URL tohttp://localhost:8080orhttp://internal-service.local. - Server-side Action: The server sends the crafted request to the internal system, exposing it to the attacker.
- Result: The attacker can now retrieve sensitive information from internal resources or even perform actions like accessing private APIs, retrieving metadata, or triggering services without authorization.
Potential Consequences of SSRF
The impact of SSRF attacks can be devastating depending on the system architecture and security posture of the target application. Here are some of the critical risks associated with SSRF:
- Bypass Network Filters: SSRF allows attackers to bypass IP whitelists or firewalls that would otherwise block external requests, giving them access to internal services.
- Internal Network Exposure: If the target application has access to an internal network or cloud environment (e.g., Amazon Web Services, Google Cloud, or Azure), an attacker can exploit SSRF to target resources that are otherwise protected from the outside world.
- Cloud Metadata Access: In cloud environments, SSRF can be used to access sensitive metadata about cloud resources, such as API keys, credentials, and configuration information. For example, in AWS, SSRF can be used to query the EC2 metadata service (
http://169.254.169.254), which might allow attackers to obtain IAM roles, secret keys, and other privileged information. - Privilege Escalation: Attackers can use SSRF to make requests on behalf of an authenticated server, potentially gaining unauthorized access to internal APIs, databases, or services that are not accessible externally.
- Denial of Service (DoS): SSRF can also be used to target internal services with a large volume of requests, leading to a denial of service by overwhelming resources or causing service disruptions.
Detecting SSRF Vulnerabilities
Detecting SSRF vulnerabilities can be tricky since the attack leverages legitimate server-side functionality to make requests. However, there are a few key indicators to help identify SSRF:
- URL or IP Address Input: Applications that allow users to input URLs, IP addresses, or similar network locations should be closely scrutinized. Any feature that fetches content from user-provided resources is a potential target.
- Network Traffic Anomalies: Analyzing server logs and network traffic can help detect unusual internal requests that might indicate SSRF exploitation.
- Cloud Metadata Requests: Monitoring for unexpected requests to cloud metadata endpoints (e.g.,
169.254.169.254for AWS,169.254.169.254for GCP) can highlight potential SSRF attacks targeting cloud resources. - Unvalidated Redirects: Check if the application redirects or forwards users to URLs they provide, especially if the application’s functionality can be manipulated to perform requests on behalf of the user.
Mitigating SSRF Vulnerabilities
While SSRF attacks are dangerous, they are preventable with proper input validation, network segmentation, and security best practices. Here are some effective strategies to mitigate SSRF risks:
- Input Validation and Sanitization: Always validate and sanitize user inputs, especially URLs or IP addresses. Ensure that only properly formatted and authorized URLs are allowed, and consider restricting input to a set of predefined, safe domains or IPs.
- Allowlisting: Use allowlists (whitelists) to restrict which URLs or IP addresses the application can access. This helps block requests to internal or sensitive resources.
- Restrict Internal Network Access: Prevent the application from accessing internal services or metadata endpoints. Use firewalls or security groups to restrict access to sensitive internal resources.
- Use Safe Libraries: When implementing features that fetch data from external resources, use secure and well-maintained libraries that have built-in protections against SSRF attacks.
- Implement Network Segmentation: Use network segmentation and firewalls to ensure that internal services are isolated and cannot be accessed from public-facing servers.
- Monitor and Audit: Regularly audit application logs for suspicious activities, such as unexpected requests to internal services or metadata APIs, and set up alerts for any anomalies.
Conclusion
Server-Side Request Forgery (SSRF) is a powerful and dangerous vulnerability that can lead to data breaches, internal network compromise, and even full system takeover. By understanding how SSRF works, recognizing the risks, and applying proper mitigation strategies, you can safeguard your systems from this serious security threat.
Remember, thorough input validation, network segmentation, and proactive monitoring are key to defending against SSRF. As attackers continue to refine their techniques, staying ahead with a robust security posture will ensure your applications remain secure from this and other emerging threats.