Introduction
XML External Entities (XXE) vulnerabilities pose a severe risk to applications that process XML data. If an XML parser is improperly configured, attackers can exploit external entity references to gain unauthorized access to sensitive information, conduct server-side request forgery (SSRF) attacks, or even execute remote code. This blog explores XXE vulnerabilities in depth, covering their causes, real-world impacts, detection methods, and comprehensive mitigation strategies.
What is an XXE Vulnerability?
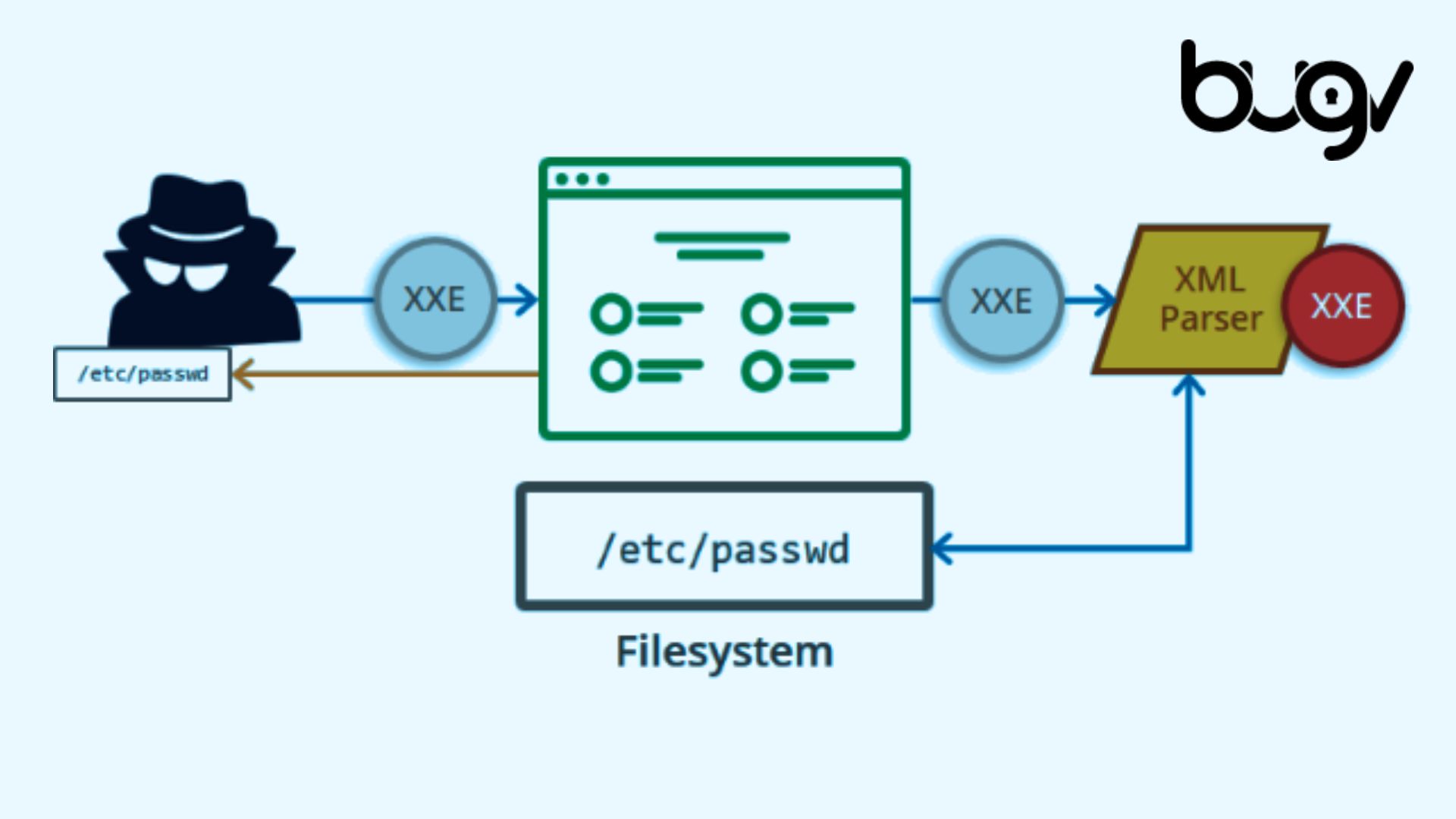
XXE is a security vulnerability that occurs when an application processes XML input containing references to external entities. Attackers can manipulate these external entities to read local files, exfiltrate data, execute code, or make unauthorized network requests.
Consider the following example of a vulnerable XML input:
<?xml version="1.0"?>
<!DOCTYPE data [
<!ENTITY xxe SYSTEM "file:///etc/passwd">
]>
<data>&xxe;</data>If the XML parser does not prevent external entity processing, it will replace &xxe; with the contents of /etc/passwd, potentially exposing user credentials and other sensitive data.
Common Exploits and Attacks
XXE vulnerabilities can be exploited in various ways, depending on the application’s architecture and the attacker’s intent:
1. File Disclosure
Attackers can exploit XXE to read arbitrary files on the server, including sensitive configuration files, database credentials, and application source code. This can lead to information leakage and further system compromise.
2. Server-Side Request Forgery (SSRF)
By manipulating XML entities, an attacker can force the server to make unauthorized requests to internal services or external endpoints. This can be used to scan internal networks, exfiltrate data, or even exploit other vulnerabilities within the network.
3. Denial of Service (DoS) Attacks
A well-known DoS exploit using XXE is the “Billion Laughs Attack.” This involves recursive entity expansion, which can overwhelm memory and CPU resources, causing the application to crash.
Example:
<?xml version="1.0"?>
<!DOCTYPE lolz [
<!ENTITY lol "LOL">
<!ENTITY lol1 "&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;">
<!ENTITY lol2 "&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;&lol1;">
<!ENTITY lol3 "&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;">
]>
<lolz>&lol3;</lolz>4. Remote Code Execution (RCE)
In rare cases, XXE vulnerabilities can be chained with other exploits to achieve RCE. If an XML parser allows dynamic execution of external scripts, an attacker might be able to execute arbitrary commands on the server.
Real-World XXE Attacks
XXE vulnerabilities have been responsible for numerous high-profile security incidents. Some notable examples include:
- Samsung SmartThings (2017): A critical XXE vulnerability allowed attackers to extract sensitive user information from the cloud.
- Yahoo! (2013): A researcher exploited an XXE vulnerability in Yahoo’s system to access internal files and won a significant bug bounty.
- WordPress Plugins: Several WordPress plugins have suffered from XXE vulnerabilities, exposing millions of websites to data breaches.
How to Prevent XXE Attacks
Organizations can adopt the following measures to mitigate XXE vulnerabilities effectively:
1. Disable External Entity Processing
Most XML parsers enable external entity processing by default. It should be explicitly disabled to prevent XXE attacks.
SAXParserFactory factory = SAXParserFactory.newInstance();
factory.setFeature("http://xml.org/sax/features/external-general-entities", false);
factory.setFeature("http://xml.org/sax/features/external-parameter-entities", false);
from lxml import etree
parser = etree.XMLParser(resolve_entities=False)2. Use Secure XML Parsers
Use modern, secure XML parsers such as DefusedXML (Python) and Secure Processing mode in Java to prevent XXE exploitation.
3. Validate and Sanitize Input
Applications should restrict user-supplied XML input and implement strict input validation to reject unexpected XML elements.
4. Use JSON Instead of XML
If possible, switch to JSON-based data formats, as they are not vulnerable to XXE attacks.
5. Employ Web Application Firewalls (WAFs)
A robust WAF can detect and block XXE-based attacks in real-time, adding an extra layer of security.
Detecting XXE Vulnerabilities
To identify XXE vulnerabilities, organizations should:
- Conduct Penetration Testing: Use tools like Burp Suite, OWASP ZAP, and Nikto to scan for XXE vulnerabilities.
- Perform Static Code Analysis: Identify insecure XML parsing methods in the codebase.
- Run Dynamic Security Testing: Simulate real-world attack scenarios to detect XXE vulnerabilities.
Conclusion
XML External Entities (XXE) vulnerabilities are a serious threat to web applications, leading to data breaches, server-side request forgery, and denial-of-service attacks. By disabling external entity processing, using secure parsers, validating input, and employing penetration testing, organizations can effectively mitigate XXE risks.
At Bugv, we specialize in identifying and mitigating vulnerabilities like XXE through expert penetration testing and security assessments. Secure your applications today by partnering with our cybersecurity professionals.
Stay updated with the latest security trends—follow us at bugv.io for more insights and best practices!