The Most Common SQL Injection Attacks
SQL Injection (SQLi) remains one of the most prevalent and dangerous vulnerabilities in web applications. Despite advancements in security, attackers continually exploit SQLi to access sensitive information, compromise databases, and disrupt services. Understanding the different types of SQL injection attacks can help developers and security professionals better protect their applications.
1. In-band SQL Injection

In-band SQL injection is the most straightforward and commonly used method. It involves the attacker inserting malicious SQL code directly into an input field that the application processes. This type of attack typically happens in two forms:
- Error-based SQL Injection: Attackers use error messages returned by the database to gather information about the database structure. By causing the database to generate error messages, attackers can gain insights that help them refine their attacks.
- Union-based SQL Injection: This method involves using the
UNIONSQL operator to combine the results of two or more SELECT statements into a single result. Attackers can use this technique to retrieve data from different database tables and columns.
Example of an In-band SQL Injection:

The -- signifies a comment in SQL, effectively nullifying the password check.
2. Error-Based SQL Injection
Error-based SQL injection is a subcategory of in-band SQLi where the attacker relies on error messages from the database to extract information. When an application is not properly configured to hide error details, attackers can use this information to understand the database schema and devise further attacks.
For Example:
![]()
If the attacker inputs:
![]()
The database might return an error message revealing the SQL Server version.
3. Union-Based SQL Injection
Union-based SQL injection is another in-band technique that uses the UNION SQL operator. By appending a malicious UNION query, the attacker can combine results from multiple queries into a single output, which might include sensitive information.
For example:
![]()
If successful, this query retrieves data from both the users and credit_cards tables.
4. Inferential (Blind) SQL Injection

Inferential SQL injection, also known as Blind SQL injection, is more challenging because it doesn’t rely on error messages or combined query results. Instead, attackers ask the database true or false questions and infer the results based on the application’s behavior.
There are two main types of Inferential SQL Injection:
- Boolean-based Blind SQLi: The attacker manipulates a SQL query to return a boolean result (true or false) and observes the application’s response to infer information about the database.
- Time-based Blind SQLi: The attacker uses database functions that cause a delay in the response (e.g.,
SLEEPin MySQL) to infer if a certain condition is true based on the time it takes for the database to respond.
Example of Boolean-based Blind SQLi:
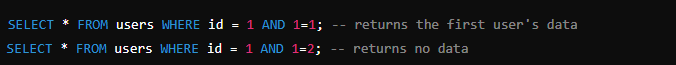
If the application behaves differently based on these queries, it can indicate the presence of a vulnerability.
Mitigation Strategies
To protect against SQL injection attacks, consider the following strategies:
- Use Prepared Statements (Parameterized Queries): These ensure that user inputs are treated as data and not executable code.
- Employ Stored Procedures: Encapsulate SQL statements within stored procedures to limit the ways SQL queries can be constructed and executed.
- Implement Robust Input Validation: Validate and sanitize all user inputs to ensure they conform to expected formats and values.
- Use ORM (Object-Relational Mapping) Tools: These abstract the SQL queries and provide a layer of security against injection attacks.
- Least Privilege Principle: Grant the minimal necessary database permissions to reduce the potential impact of an injection attack.
SQL injection remains a significant threat, but by understanding and implementing these mitigation strategies, developers can significantly reduce the risk and protect their applications from exploitation.
For more details on SQL injection attacks and how to prevent them, visit bugv.io.











