Insecure Direct Object Reference (IDOR) is a security vulnerability that arises when attackers gain unauthorized access or manipulate objects by exploiting identifiers in a web application’s URLs or parameters. This occurs due to inadequate access control checks, failing to verify whether a user has the proper authorization to access specific data.
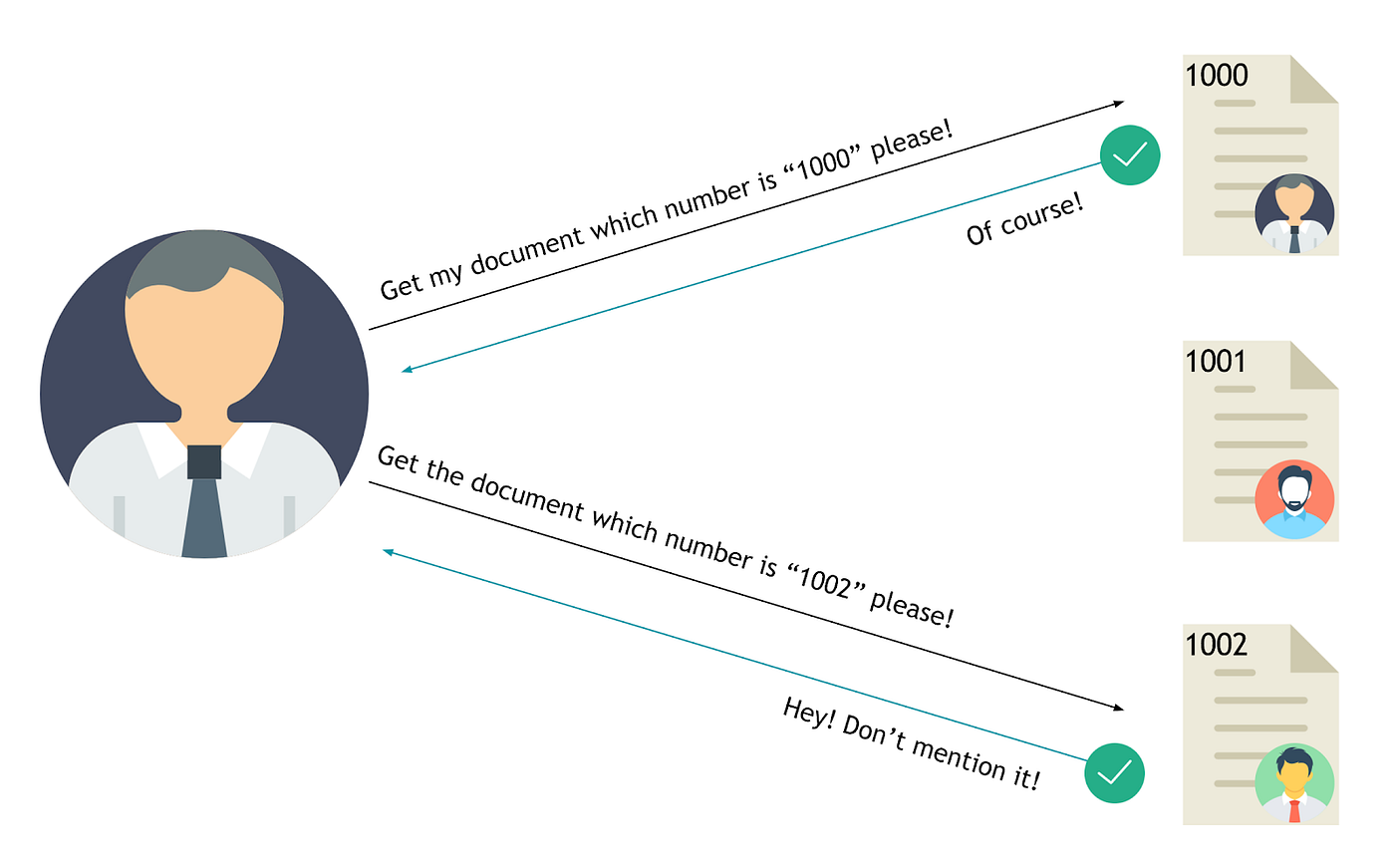
Consider a scenario where a web application displays transaction details through a URL, like:
https://www.payment-application.com/transaction.php?id=1341
A malicious actor might attempt to tamper with the `id` parameter, substituting values like 1342:
https://www.payment-application.com/transaction.php?id=1342
Depending on the application’s implementation, transaction 1342 might belong to another user account, and the unauthorized hacker should not have access. If the developer neglects to enforce proper authorization checks, the attacker could exploit this vulnerability, leading to an insecure direct object reference.
Types of IDOR Attacks:
1. URL Tampering:
Exploiting IDOR vulnerabilities through URL tampering is a simple method that requires minimal technical expertise. Attackers can easily change parameter values in the web browser’s address bar.
2. Body Manipulation:
Similar to URL tampering, body manipulation involves modifying values within the document’s body, such as radio buttons, checkboxes, or hidden form elements.
3. Cookie or JSON ID Manipulation:
Attackers can manipulate Cookies or JSON objects, altering values like user or session IDs stored between the client and server, potentially exploiting IDOR vulnerabilities.
4. Path Traversal:
Path traversal, a unique form of IDOR, enables attackers to directly access or manipulate files and folders on the server, providing deeper access than other types of IDOR attacks.
Detecting IDOR Vulnerabilities:
1. Look for Integer Values:
Examine features and their functionalities. Manipulating integer values, such as order IDs, in URLs may reveal unauthorized access to sensitive information.
2. Updating Account Settings:
Manipulating parameters related to account settings, especially during updates, might lead to the unintended editing of another user’s profile.
3. Querying for Information:
During processes like checkout, parameter-controlled requests may expose sensitive user information. Even if parameters are not apparent, testing with common identifiers is recommended.
Impacts of IDOR Vulnerability:
1. Exposure of Confidential Information:
Unauthorized access can lead to exposure of personal information.
2. Authentication Bypass:
IDOR can function as an authentication bypass mechanism, granting access to numerous accounts.
3. Alteration of Data:
Attackers may manipulate and alter user data, potentially leading to record manipulation.
Remediating IDOR Vulnerability:
– Avoid Displaying Private Object References:
Developers should refrain from displaying private references like keys or file names.
– Implement Proper Parameter Validation:
Ensure validation of parameters to prevent unauthorized access.
– Verify All Referenced Objects:
Thoroughly verify all referenced objects to strengthen security.
– Secure Token Generation:
Generate tokens that are exclusively mapped to individual users and not publicly accessible.
– Use Random Identifiers:
Employ random identifiers to enhance the difficulty of guessing by potential attackers.
– Implement Rigorous User Input Validation:
Ensure robust validation of user inputs to thwart potential exploitation of vulnerabilities.
In summary, Insecure Direct Object Reference (IDOR) vulnerabilities pose significant threats to web applications, allowing unauthorized access and manipulation of sensitive data. The diverse range of IDOR attacks, from URL tampering to path traversal, underscores the importance of robust security measures.
If you are interested and want to learn about the vulnerability then do visit Portswigger Web Academy Labs on IDOR at https://portswigger.net/web-security/access-control/idor