In the dynamic world of cybersecurity, organizations are constantly on the lookout for vulnerabilities within their systems. Two prevalent methods used to uncover these vulnerabilities are Penetration Testing (Pen Testing) and Bug Bounty Programs. While both aim to identify and mitigate security risks, they differ significantly in their approach, incentives, and overall methodology. This blog explores these differences in detail to help you understand which might be more suitable for your organization.
Pen Testing: Structured and Comprehensive
Pen Testing is a systematic approach to identifying vulnerabilities within a specific scope. Here’s a closer look at its key characteristics:
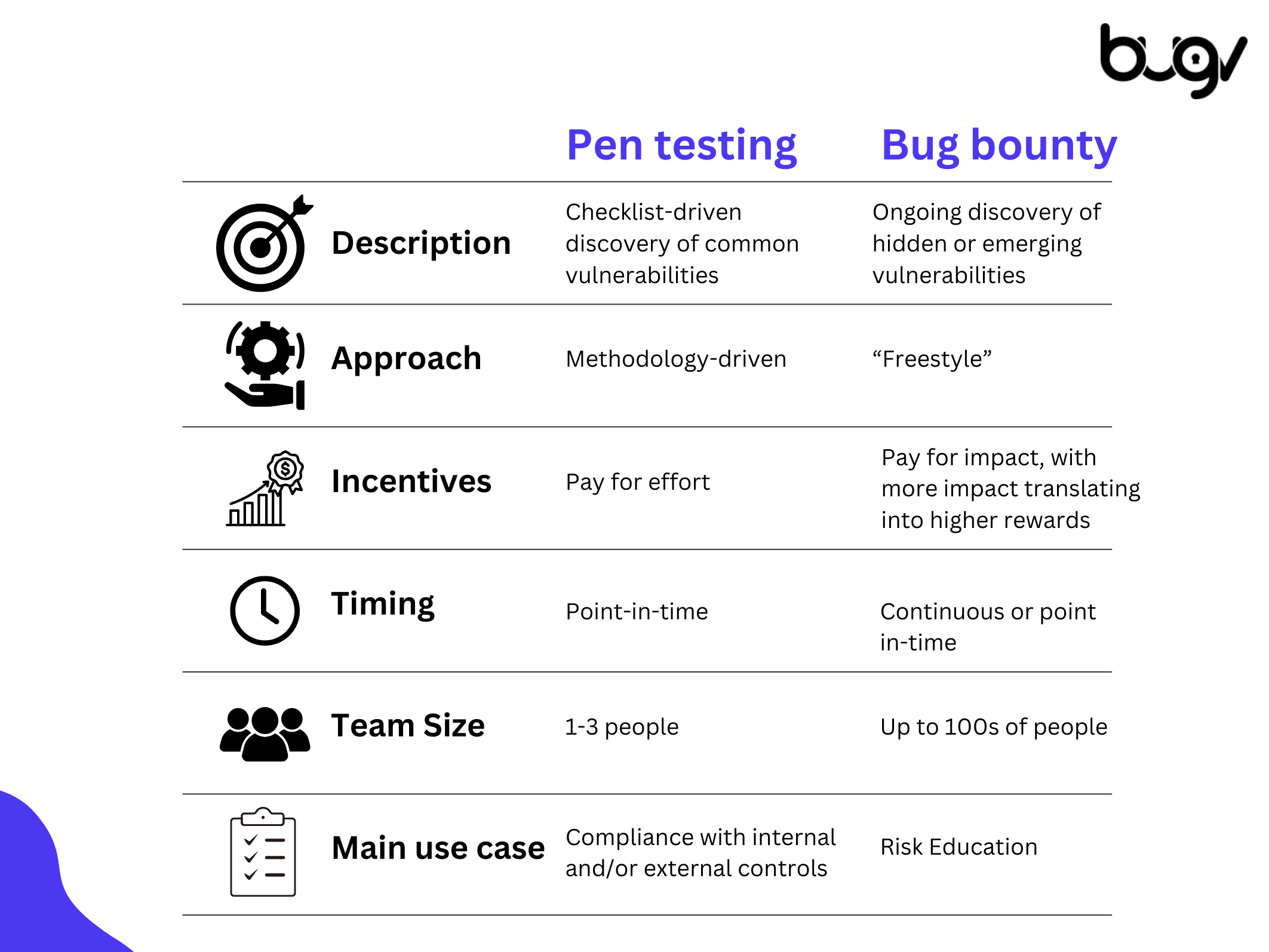
⦁ Description: Pen testing involves a checklist-driven discovery of common vulnerabilities. This means that testers follow a predefined list of potential security weaknesses, ensuring a thorough examination of known issues.
⦁ Approach: The methodology-driven approach of pen testing means that testers use established procedures and protocols. This ensures consistency and comprehensiveness in the testing process.
⦁ Incentives: Testers are typically compensated for their effort, regardless of the number or severity of the vulnerabilities they uncover. This pay-for-effort model provides a steady income for security professionals.
⦁ Timing: Pen testing is usually conducted at a specific point in time. This could be part of a routine security audit or in response to a significant update or change in the system.
⦁ Team Size: Pen testing teams are relatively small, usually comprising 1-3 highly skilled professionals who specialize in identifying and exploiting security weaknesses.
⦁ Main Use Case: The primary objective of pen testing is to ensure compliance with internal and/or external controls. This makes it particularly useful for organizations that must adhere to regulatory standards and industry best practices.
Bug Bounty Programs: Agile and Ongoing
Bug Bounty Programs, on the other hand, offer a more flexible and continuous approach to uncovering security vulnerabilities:
⦁ Description: Bug bounty programs focus on the ongoing discovery of hidden or emerging vulnerabilities. This allows for the identification of issues that may not be covered by standard checklists.
⦁ Approach: Unlike the structured approach of pen testing, bug bounty programs operate on a “freestyle” basis. Security researchers have the freedom to explore and test in any manner they see fit, often leading to the discovery of novel vulnerabilities.
⦁ Incentives: In bug bounty programs, researchers are paid based on the impact of the vulnerabilities they find. This pay-for-impact model incentivizes the discovery of more critical and severe security issues, as higher rewards are given for more impactful findings.
⦁ Timing: Bug bounty programs can be continuous or conducted at specific points in time. This ongoing nature allows organizations to constantly monitor and improve their security posture.
⦁ Team Size: The scale of bug bounty programs can vary greatly, involving up to hundreds of independent security researchers. This vast pool of talent increases the likelihood of discovering a wide range of vulnerabilities.
⦁ Main Use Case: The primary goal of bug bounty programs is risk reduction. By continuously identifying and addressing security issues, organizations can significantly reduce the risk of cyberattacks.
Choosing the Right Approach
The decision between pen testing and bug bounty programs depends on the specific needs and goals of your organization:
⦁ Compliance Needs: If your organization needs to meet strict regulatory requirements or internal controls, pen testing is the more appropriate choice. Its structured approach ensures thorough coverage of known vulnerabilities and compliance with standards.
⦁ Continuous Security Improvement: If your organization aims to maintain a high level of security over time, bug bounty programs offer the flexibility and ongoing discovery needed to address emerging threats. The diverse pool of researchers can provide a broader perspective on potential vulnerabilities.
⦁ Resource Availability: Consider the resources available within your organization. Pen testing requires a smaller, specialized team, while bug bounty programs can leverage a larger community of researchers, potentially offering more extensive coverage.
In conclusion, both pen testing and bug bounty programs are essential tools in the cybersecurity arsenal. Understanding their differences and unique advantages allows organizations to tailor their security strategies to best protect their assets and data. By integrating both approaches, businesses can achieve a robust and comprehensive security posture, mitigating risks and ensuring compliance in an ever-evolving threat landscape.
Bugv is specialized in VAPT (Vulnerability Assessment and Penetration Testing) and Penetration Testing, ensuring your start-up’s security is robust and reliable. We also offer a unique crowdsourcing platform where you can launch your own Vulnerability Disclosure Program (VDP). A VDP allows ethical hackers to identify and report security vulnerabilities in your systems before malicious actors can exploit them, enhancing your security posture significantly. Additionally, our Bug Bounty Program incentivizes security researchers to find and disclose vulnerabilities, providing an extra layer of protection for your start-up. Secure your start-up effectively with these comprehensive security solutions. If you’d like to know more about our services and solutions, please reach out to us at ‘support@bugv.io’ or contact us directly.
You can sign up for your account at bugv.io to start enhancing your security today.











